If a DMZ (DeMilitarised Zone) structure makes data storage - in particular the key management - within the network location of the email processing system inadmissible, the frontend/backend cluster offers the possibility to separate the database from the email-processing system.
This means that, with this specific form of a SEPPmail Secure E-Mail Gateway cluster, no configuration database exists on the system which is configured as the frontend. The configuration data required for the runtime is stored exclusively on the backend system hosting the configuration database, and thus also the key material, and pushed to the frontend system upon a corresponding request by the latter in the push procedure (purple arrows in "Figure 7").
By terminating the action requested on the frontend system – for example, encryption or decryption – the configuration data requested for this purpose is automatically discarded/deleted.
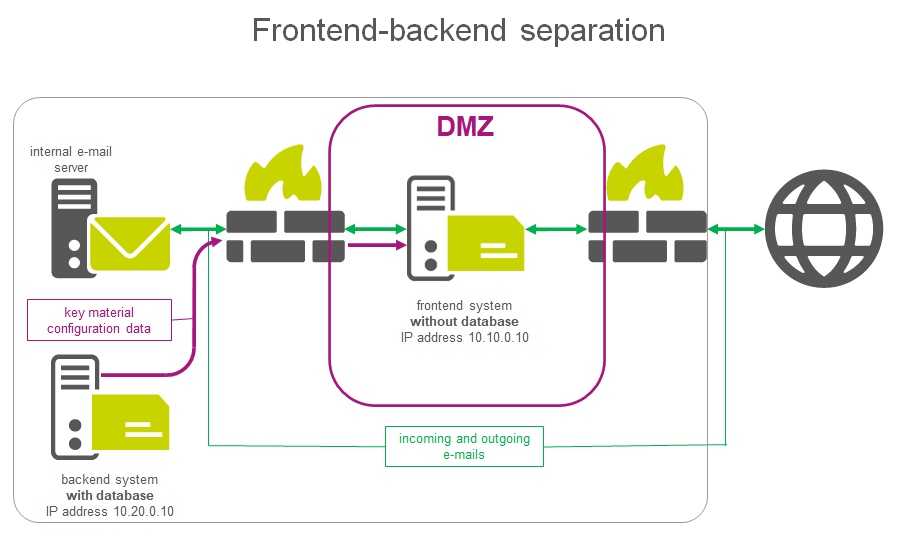
Figure 7 - Schematic representation of a frontend/backend cluster structure
In this constellation, a special case is given if the Large File Transfer (LFT) is active at the same time. Since the provision of large data volumes of an LFT message would inevitably lead to a slower performance in the event of a request by the external recipient via the SSH tunnel from the backend to the frontend, free disk space on the frontend system would also need to be provided for the LFT. Here, the frontend system maintains the synchronisation with the backend so that no additional port releases (please also refer to Setting Up The Firewall/Router) are required.