Since email systems usually only communicate via SMTP port 25, under certain circumstances and due to an existing DMZ (DeMilitarised Zone) structure, the communication required for the GINA technology via SSL port 443 may not be possible. To be able to use the GINA technology nonetheless, without having to weaken the security infrastructure, it is possible to separate this technology via the GINA satellite system andthus place it outside of the DMZ. There are generally two options available in this respect.
This basically corresponds to the Frontend/Backend Cluster, in which the frontend system exclusively takes over the GINA function.
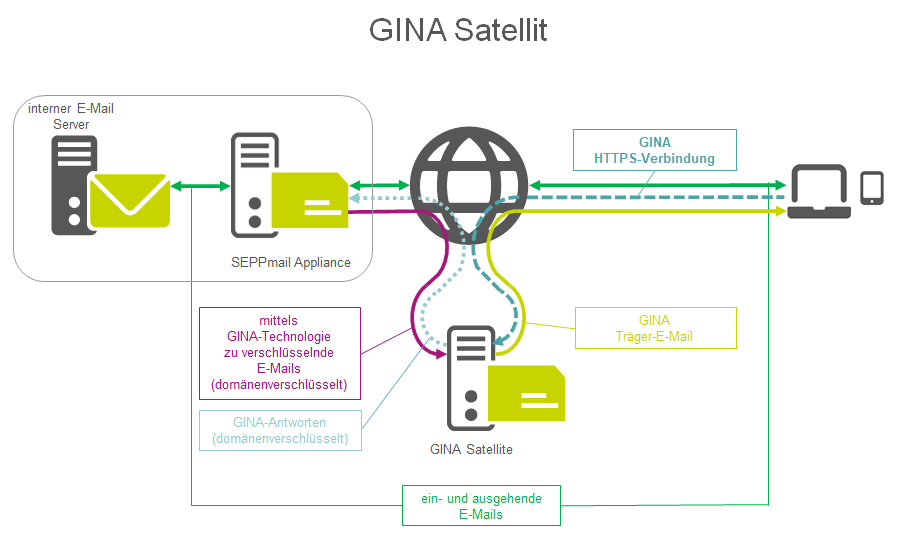
Figure 8 - Schematic representation of a secure webmail satellite structure in a DMZ
Variant 2
(no longer supported as of version 12.1.7!)
The communication between the base system and the satellite system takes place via SMTP port 25 (purple arrow in "Figure 8"). To the Internet, the GINA web interface is usually provided separately via a web application firewall (WAF) via SSL port 443.
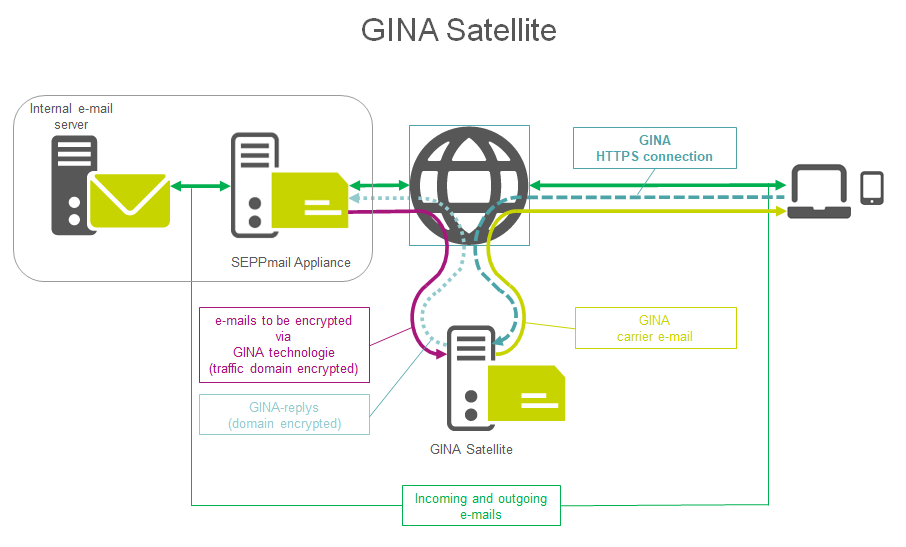
Figure 8a - Schematic representation of a secure webmail satellite structure with an external satellite system
(new in 12.0)
If the GINA is to be operated purely as a web server, i.e. external access to the machine is possible, but the system itself may not communicate with the outside, emails may be temporarily stored on the satellite system after being processed there. In this case, the backend system would collect the emails stored temporarily on the satellite system via POP3s (see orange arrow in "Figure 8b") and process them further.
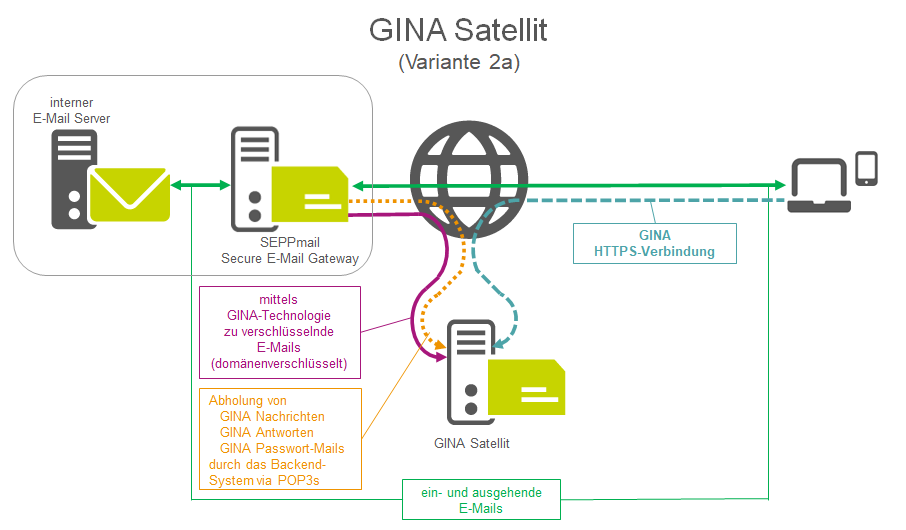
Figure 8b - Schematic representation of a secure webmail satellite structure with an external satellite systemwithout any external communication