The SEPPmail Secure E-Mail Gateway instance uses ARC sealing. Every ARC seal is done with the master ARC key of the Gateway.
Mail flow:
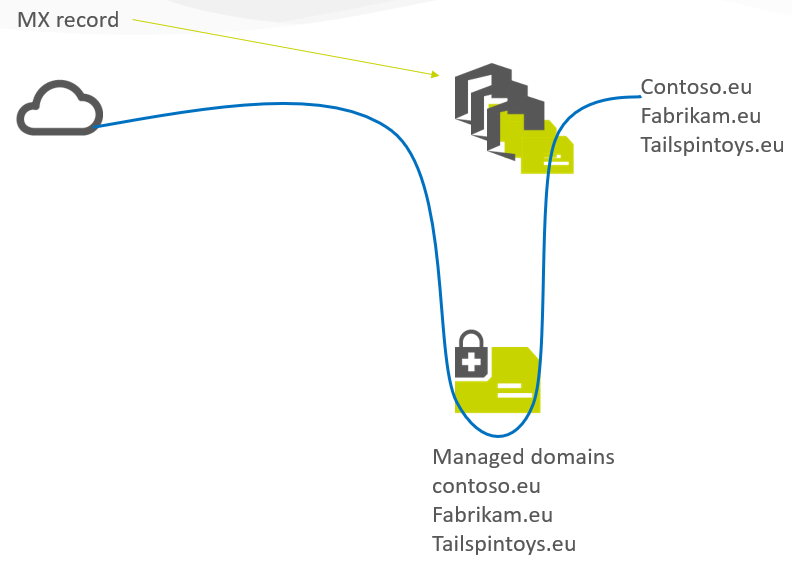
Setup:
•Mail System > Add ARC seal to incoming mails
•Domain: enter a domain whose DNS is under the control of the MSP
•Selector: "default"
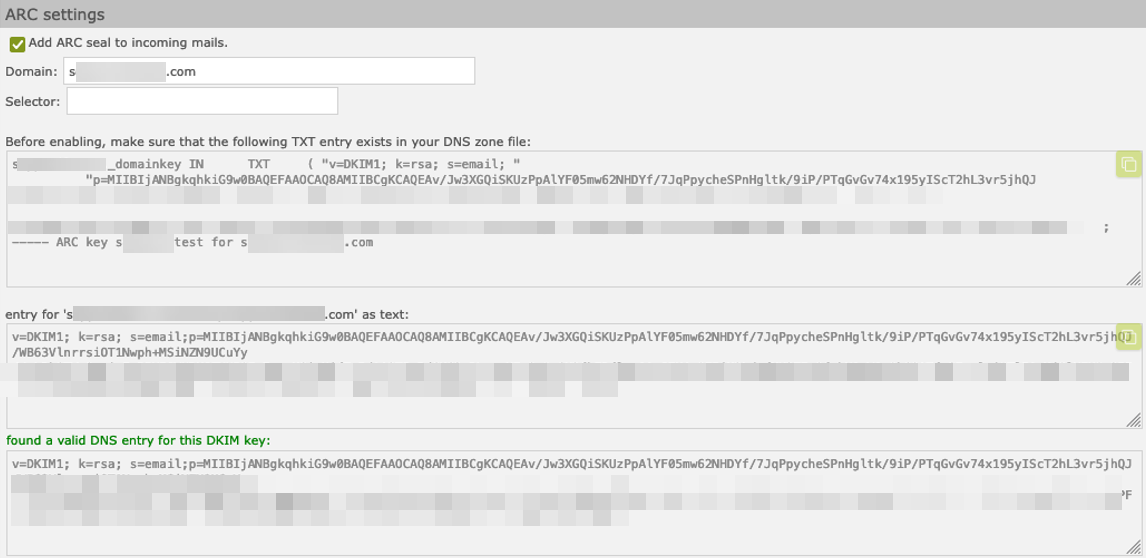
Settings for each domain:
•Add ARC seal to incoming mails for this domain
•Key source: Use the master ARC key
 Note regarding SPF-Record: hard fail
Note regarding SPF-Record: hard fail
ARC seals are ignored in general by Microsoft if the setting SPF record: hard fail is enabled in one of the Antispam Policies!
Reason:
In Exchange Online Protection (EOP), when you configure the antispam policy with the "SPF record: hard fail" setting, it means that emails failing SPF validation with a hard fail mechanism ('-all') in their SPF record will be treated as spam or rejected.
ARC (Authenticated Received Chain) is a mechanism used to preserve email authentication results across intermediaries, such as mailing lists or forwarding services. It's designed to address issues that SPF, DKIM, and DMARC face when an email is forwarded or handled by multiple mail servers.
When Exchange Online Protection evaluates an email, it checks the SPF record of the sending domain. If the SPF record has a hard fail mechanism ('-all') and the email fails SPF validation, it will be treated according to the policy you have configured. The ARC seal, if present, provides additional context about the authentication results from previous hops. However, the presence of an ARC seal does not supersede the SPF hard fail result.
So if an email fails SPF validation with a hard fail ('-all') and your antispam policy is configured to treat such failures as spam or reject them, Exchange Online Protection will follow that policy regardless of the ARC seal.
https://security.microsoft.com/antispam
Policies & rules > Threat policies > Anti-spam policies
PowerShell check:
# MarkAsSpamSpfRecordHardFail should NOT be set
Get-HostedContentFilterPolicy Default | Select-Object MarkAsSpamSpfRecordHardFail
MarkAsSpamSpfRecordHardFail
---------------------------
Off
Screenhot with example entry "Inbound alles EIN [SEPPmail]":
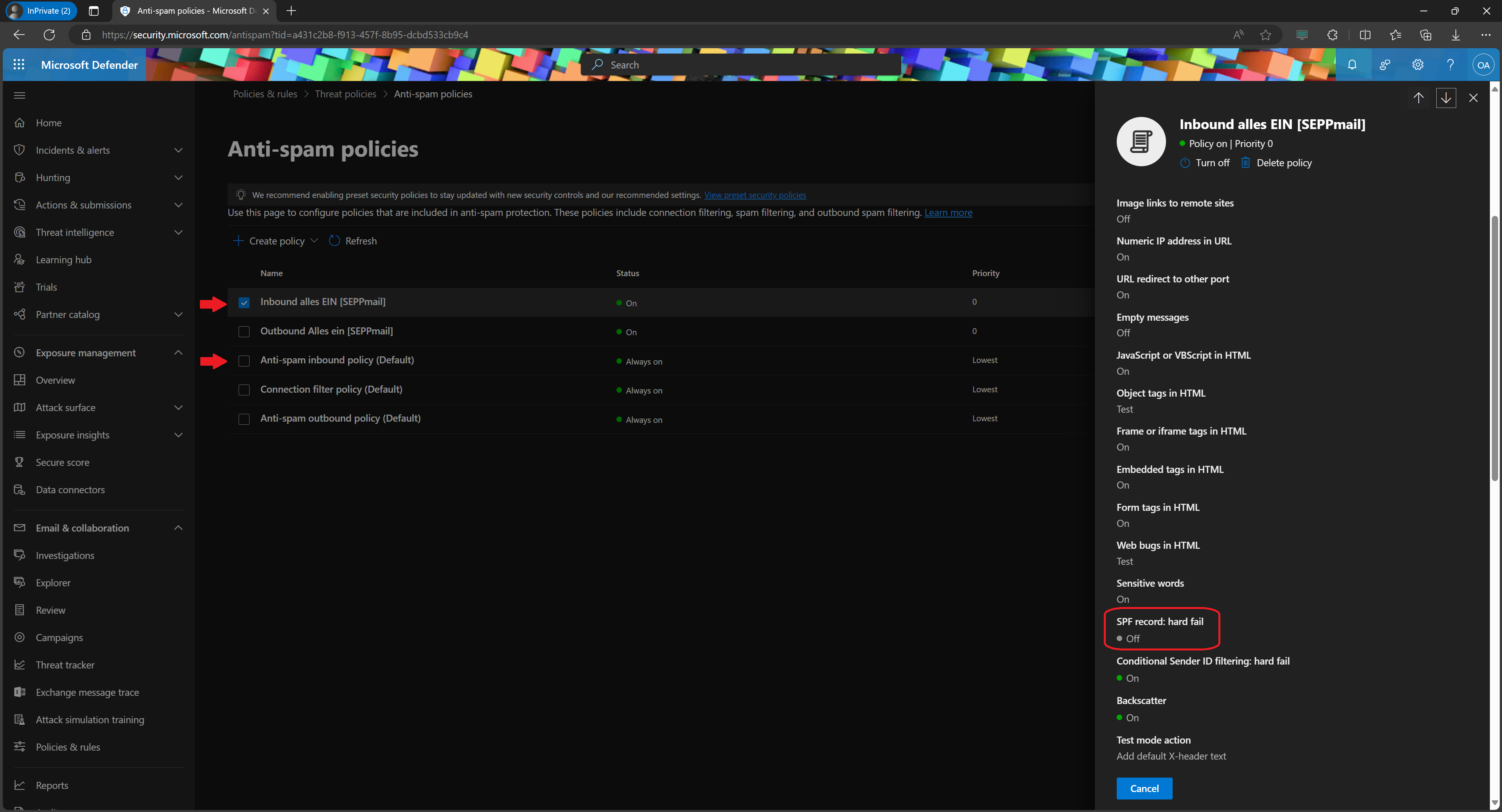
|
Note: When creating the connectors and rules via the PowerShell Modul SEPPmail365, no policies are created or changed. |
