Initial situation:
For example, several SMTP access points with authentication are to be provided on a client-capable system instead of a Relaying entry for forwarding emails of the customer groupware server to the SEPPmail Secure E-Mail Gateway.
Solution:
1.Create a (pseudo) Managed domain – e.g. "pseudo.local" – with the IP address [127.0.0.1] as Forwarding server entry (Mail System Managed domain Add domain... Settings Forwarding server IP or MX name).
2.Mail System Antispam Recommended settings: PTR check and Optional settings: Strict PTR check deactivate if active.
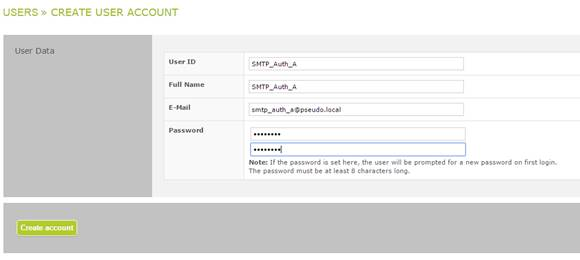
3.Creation of one user for each SMTP authentication required (client)
Administration interface Users Create new user account User Data.
Example
Access client A
Access client B
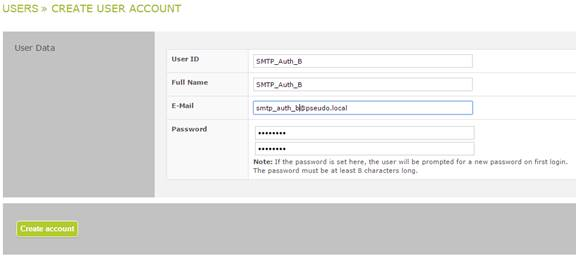
and so on.
At the respective groupware system, the SEPPmail Secure E-Mail Gateway now has to be entered as the SMTP server "smtp_auth_a@pseudo.local" - i.e. the email address of the created user - with the assigned password as a user for "Access client A" or "smtp_auth_b@pseudo.local" with the assigned password as a user for "Access client B" and so on.
To ensure that these (pseudo) users do not take up a user licence on the appliance, we recommend withdrawing the right to cryptographic treatment of emails from these (login) users.
For this purpose, in the administration interface under Users, click on the corresponding user (in the example SMTP_Auth_A and SMTP_Auth_B) and, in the subsequent menu in the section User Data in Encryption settings, set the checkmark for the options May not encrypt mails and May not sign mails.
If authentication is to use TLS-secured connections exclusively, the option Require TLS encryption under Mail System SMTP settings is to be activated.
It is to be ensured that no protection component (e.g. firewall) between the client and the SEPPmail Secure E-Mail Gateway is blocking the Auth login by SMTP proxying.