To help you, here is a step-by-step guide to creating the desired function. Possible additional functionalities are not considered here.
The degree of the safety measures set here must, if necessary, be determined by the operator of the SEPPmail Secure E-Mail Gateway themselves and be adapted to their circumstances.
|
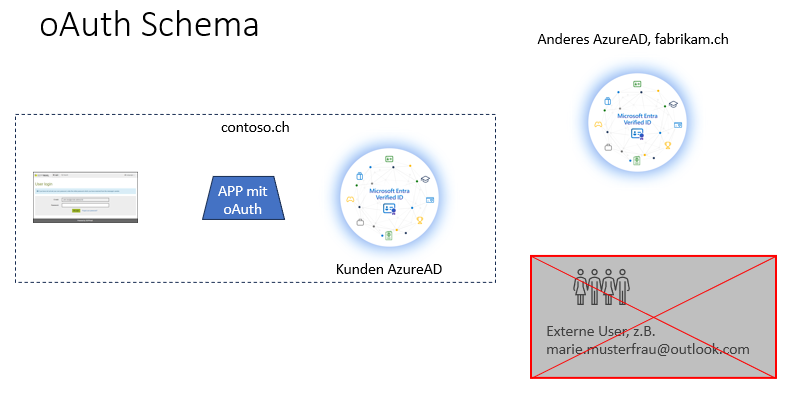
Note: Currently, Microsoft OAuth can only be used to authenticate external communication partners who belong to a Microsoft Entra ID / Entra Domain Services (formerly Azure Active Directory - AAD). |
Procedure:
(As of 12.07.2023)
Microsoft-sided Configuration
•Login at the Microsoft 365 admin center (https://admin.microsoft.com/) as a user with at least the role "Cloud application administrator".
•In the navigation menu on the right (if necessary, click "Show all...") under "Admin centers", click on "Entra Domain Services". The "Dashboard" opens.
•To the right of "Dashboard", again click on "Entra Domain Services". Under "Dashboard", the "Overview" opens.
•To the right, click on "App registrations".
•Clicking on the tab "+ New registration" opens the menu "Register an application".
oUnder "*Name", enter a descriptive name for the future connection.
(The name should be noted in parallel as "IDP service name".)
|
Note: The APP name is later displayed in the GINA GUI when accessing the user data. A name that clarifies the purpose and origin of the APP is therefore recommended, for example •contoso.eu - Secure E-mail •contoso.eu - GINA Login
|
oTo ensure that only users of one's own organisation, i.e. of one's own AAD, can authenticate themselves via this variant, it is necessary to select under "Supported account types" the entry "Accounts in any organizational directory (Any Azure AD directory - Multitenant)".
With this setting, all user accounts of any AAD can authenticate themselves. This means that any user with an M365/Exchange online account can log in.
oUnder "Redirect URI" in the drop-down menu "Select platform", select "Web" and as "URI" enter the full URL of the corresponding GINA Domain as displayed in the note "Note: If you want to show the GINA login page by default, enter "https://.../web.app" (without the quotes)" above the input field Default Forward Page.
|
If the access should be used for several GINA Domains, their "URI" might be entered later. |
oFinally click on "Register" .
(The "Application ID" (NOT the Object ID !) should be noted in parallel as "ID").
•In the side menu of the "Dashboard", click on "API permissions".
oIn the "Configured permissions" displayed to the right, in the table below under "API / Permissions name" "Microsoft Graph" and below of this, usually the authorisation "User.Read" is displayed.
oBy clicking " + Add a permission", "Request API permissions" opens to the right.
oThere on the tab "Microsoft APIs" from the "Commonly used Microsoft APIs", select "Microsoft Graph".
oIn the next menu, select "Application permissions" and in the area below "Select permissions", open "User". There, select "User.Read.All". Finish by clicking the "Add permission" button.
•The menu "API permissions" is displayed.
Under "API / Permissions name" "Microsoft Graph", the authorisations "User.Read" and "User.Read.All" are now displayed.
•Clicking on the "Overview" in the side menu of the "Dashboard", the "Essentials" opens.
There under "Client credentials", click on "Add a certificate or secret".
oIn the next menu "Certificates & Secrets" on tab "Client secrets", click on "+ New client secret".
oTo the right, "Add a client secret" opens. Next, under "Description", enter a name that is as meaningful as possible, and under "Expires" select the desired validity date for the secret.
Finish by clicking the "Add" button.
oThe menu "Certificates & Secrets" should again appear on the tab "Client secrets". There, the newly created secret is displayed.
|
Attention: SAVE the key "Value" in a secure location, it is displayed only ONCE. |
SEPPmail Secure E-Mail Gateway-sided configuration:
•Log on to the administration interface.
•Switch to the menu GINA Domains.
•In the table of section Domains under GINA name, click on the GINA Domain.
•In the next menu , navigate to the section IDP settings.
•In the section OAuth authentication, create a new connection via New OAUTH authentication.
oCheck the option Authenticate GINA users from this domain with OAUTH to activate it.
oDepending on the case (see also GINA Webmail (optional) Initial Message Writing, as well as Large File Transfer (LFT) Delivery/Sending Via GINA Webmail, Delivery/Sending via SEPPmail Microsoft Outlook Add-In and Delivery/Sending By External Sender and for Internal Mail Encryption (IME) SEPPmail IME with the exclusive utilisation of the GINA technology and SEPPmail IME 1.0), the option Automatically create GINA account if user can authenticate with OAUTH should also be activated.
oUsed by managed domains is to be left empty.
oFill in IDP service name in the "IDP service name" with the noted down information from the Microsoft-sided configuration.
oAs Service provider, select "Microsoft".
oUnder ID fill in the "ID" with the noted down information from the Microsoft-sided configuration.
oUnder Secret fill in the "Secret" / "Value" with the noted down information from the Microsoft-sided configuration.
oUnder Login button CSS class(es), "btn-default idp-btn" should already be pre-filled.
oConfirm the configuration by clicking on Add.